Cyberattacks hit every 11 seconds
How are you going to respond in the ten seconds after an attack hits you?
Learn what you need to do to protect your business
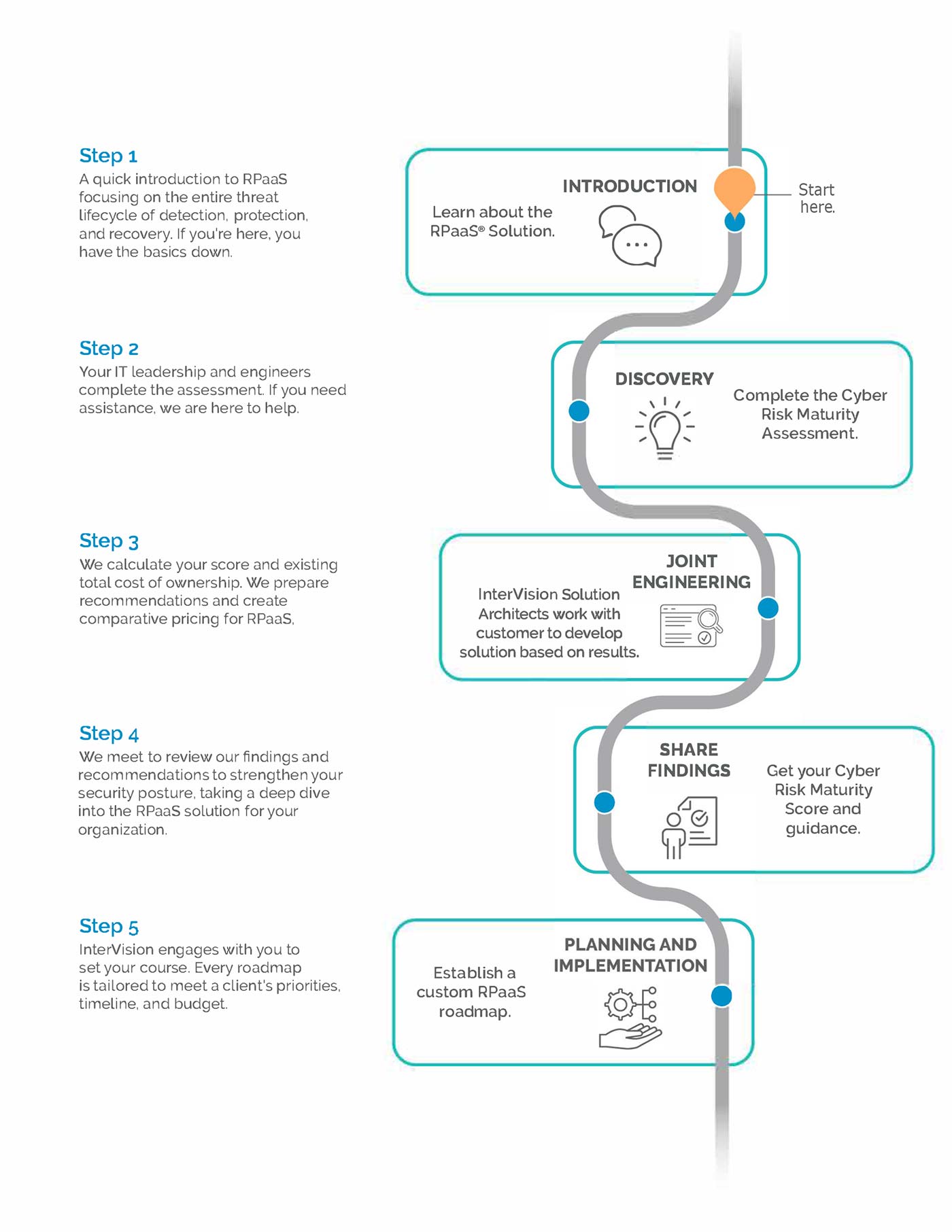
The Cyber Risk Maturity Assessment guides you through a series of questions based on cyber insurer standards and NIST methodologies.
The data collected is compared to peers and creates a set of Cyber Risk Maturity Scores that highlight risk, priority areas, and the relevant impact of a cyber incident when it occurs.
The Cyber Risk Maturity Score Report
Measure your risk quantitatively. Avoid business disruption and proactively measure your risk quantitatively to understand the probability and impact of a data breach on your business. Spend about forty minutes to an hour answering a few questions honestly. We align your answers to the 5 functions of the NIST CSF.
We deliver these items in your Cyber Risk Maturity Score Report:
- Provide a maturity score that illuminates gaps.
- Provides insight on how to improve your security posture and preparedness.
Be future-ready. No matter what. Schedule your call now.
What does the assessment process look like?
InterVision Cybersecurity Solutions
As cyber threats continue to grow in number and sophistication, it’s important to have the right level of protection in place. We offer three levels of cybersecurity solutions. Use our chart to compare features and find the right fit for your business.
Foundation | Professional | Enterprise | |
Builds a solid foundation for detection, and response to Cyber Threats. | Improves upon IV cybersecurity foundation by validating your cybersecurity plan and providing 24x7x365 professional remediation of vulnerabilities. | Adds to the IV cybersecurity professional offering with comprehensive and ongoing security posture management and recovery services to end downtime risk. | |
Managed Detection and Response (MDR) A security solution providing comprehensive threat monitoring, incident response, and expert analysis aimed at safeguarding businesses against cyber threats, serving as an alternative to an in-house Security Operations Center (SOC). | |||
Incident Response (IR) Retainer A proactive solution offering aimed at aiding in incident response plan preparation and providing priority cost-transparent incident response engagements without the need to pre-purchase hours, ensuring a 1-hour SLA response from expert engineers. | |||
Enhanced Cyber Threat Concierge Service A named resource is assigned to the account for the MDR solution to seamlessly integrate the InterVision Operations Center, Customer Success, Client Service, Professional Service, and other teams by providing regular ticket reviews, escalation, and relationship management. | |||
Penetration Testing Proactive vulnerability identification and root cause analysis through one-time or live testing and expert analysis. Continuous testing ensures ongoing risk management and business continuity while safeguarding customer and partner interests and improving ROI from security investments. | (1-time) | (Continuous) | |
Managed Device (Monitoring, Patching, Remediation) InterVision’s suite of Managed Network and Server solutions, combined with our MDR solution, provide end-to-end 24/7 expert detection, response, remediation, best practice review, and change management for client devices. | |||
Managed Helpdesk Provides personalized and effortless support, offering 24/7 access to expert personnel, industry-leading response times, and a single point of contact for all users, serving as a cost-effective alternative to in-house support. | |||
Endpoint Detection and Response (EDR) Streamlines risk mitigation, expediting threat containment, integrating malware protection, and enhancing ROI for businesses by leveraging expert detection, isolation of compromises, and proactive security measures. | |||
Monthly vCISO InterVision’s Cyber Consulting team engages with the client regularly to assist in the maturation of the client’s security profile, address business risks, and develop roadmaps for improvement. | |||
Disaster Recovery as a Service (DRaaS) Offers immediate disaster reaction, robust infrastructure protection, ongoing testing for compliance, and a customized recovery playbook, all backed by industry-leading SLAs to ensure recovery assurance. | |||
Your strategic partner for an AI-Driven future
InterVision combines technical excellence with a strategic, future-ready approach—empowering your organization to lead with confidence, agility, and results.
InterVision delivers leading AI services for every step of the journey, from getting started with AI to developing policies, leveraging hyperautomation via agentic workflows, and setting up POC environments- all aligned to your business goals.
Our team has decades of experience and hundreds of certifications with AWS, Microsoft, Cisco, Fortinet, Juniper, Arctic Wolf, HPE, and many more. No matter your challenge, InterVision can tailor innovative services using best-in-class technology solutions.
Remove obstacles to innovation and leverage InterVision expertise to take advantage of flexible financing choices, exclusive purchasing plans, and simplified marketplace transaction options.
Managed Innovation is InterVision’s unique approach to managed and professional services that drives IT excellence not just today, but into tomorrow. Our success is your success, and our expert team works diligently to continually evolve IT solutions that keep your company ahead of change.
Seamlessly navigate unforeseen IT change with pre-validated solutions from the InterVision NextMove program. Leave unwieldy vendor lock-in and unfavorable contracts behind, while pivoting to next-generations solutions that deliver better performance, costs, and outcomes.
InterVision is a trusted partner for state and local governments, K-12 schools, and higher education institutions. Our expert team can deliver pre-validated solutions and services that deliver better outcomes for constituents and meet complex regulatory challenges.