
Uncover real-time risks and prioritize remediation with RedSpy365, leaving traditional penetration tests behind.
Mitigate threats
Integrate Agger Labs’ real-time ransomware protection for continuous, adaptive security.
Find vulnerabilities
Identify root causes and gaps in regulatory compliance.
Fix liabilities
Recognize containment delays and prioritize solutions.
Understand impact
Grasp the financial and business continuity impact.
Why should you do continuous penetration testing? Watch our Explainer video.
How PTaaS works
Our solution redefines pen testing with continuous live air-gapped testing, advanced automation, best-of-breed tooling, and expert human analysts — now enhanced with Agger Labs’ real-time ransomware defense for a comprehensive security approach.
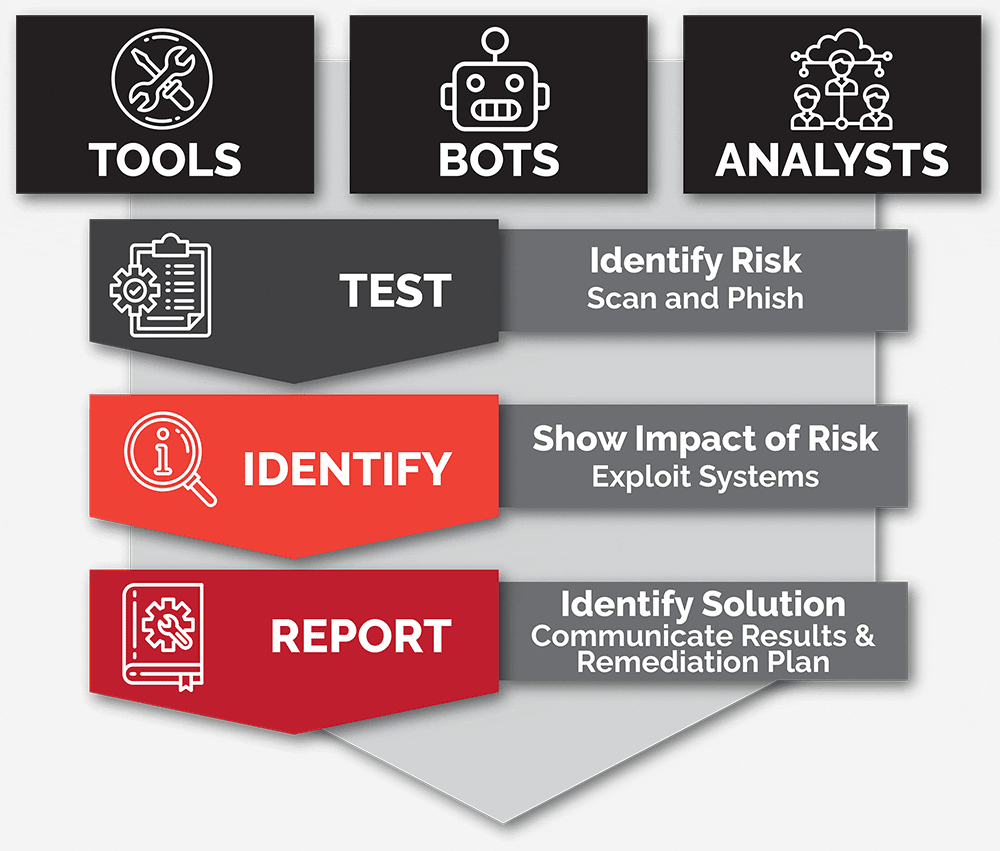
Continuous testing delivers ongoing value
As a security service, PTaaS replaces one-time tests that provide you with a snapshot of your environmental risks and converts it into a streaming video, delivering you continuous value.
- Enhanced risk management and business continuity.
- Customer and partner protection, safeguarding brand reputation.
- Prevent financial losses and improve ROI from security investments.
- Ensure security in a work-from-anywhere world while enhancing compliance.
Features we’ll cover:
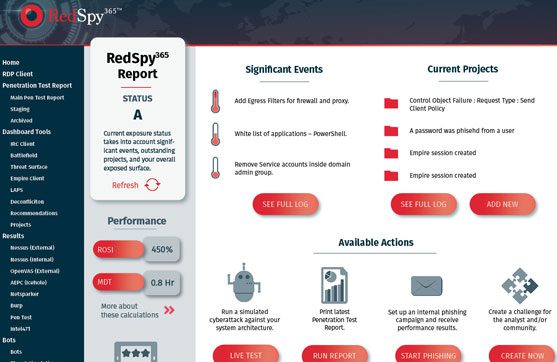
- Interactive dashboard
- On-demand reporting
- The Orchestrator
- Ecosystem of 200+ tools
You’ll learn how to:
- Easily create sophisticated attack models.
- Digest institutional knowledge to understand business risk
- Obtain auditor-ready reporting
- Navigate the ecosystem and how it differs from a platform
CASE STUDY
How a leading financial institution saved over $1 million in damages with RedSpy365
A leading financial institution deployed RedSpy365 into its environment, including a live threat feed.
The following actions were triggered by RedSpy365:
- An analyst noted bad actors targeting VMware vSphere products seeking a weaponized exploit.
- The analyst quickly built a threat scenario that mimicked the live-feed attack.
- After running the test, the institution was found to be vulnerable to exploitation.
- RedSpy365 triggered an immediate alert to the institution about the threat with the required changes to avert damage and loss.
- The RedSpy365 bots, configured with the asset inventory, generated an estimated potential economic loss of over $1 million.
63% of organizations biggest challenge is hiring qualified staff
“Redspy365 allows my team to have a non-coordinated adversary that really acts like a red team in red on blue exercises. Their creative approach, trend analysis, research, and development push us to constantly evolve and improve our security posture. In addition to allowing us to focus on our core skills of protecting and defending, their communication is top notch and personal attention is above all others that we have assessed. We are very grateful to have Redspy365 to fill a critical piece in our overall Cybersecurity puzzle.”
Chief Technology Officer, Jeffrey Potter, CISSP
Davenport & Company LLC
What does the maturity model look like?
![PTaaSJourney_V02[13]_vertical_8-29-2023](https://intervision.com/wp-content/uploads/2023/09/PTaaSJourney_V0213_vertical_8-29-2023.jpg)
Knowledge is power
Stay informed and proactive about security with Penetration Testing as a Service. Learn how penetration testing helps identify vulnerabilities before they become threats, ensuring the safety of your organization’s IT environment.
Your strategic partner for an AI-Driven future
InterVision combines technical excellence with a strategic, future-ready approach—empowering your organization to lead with confidence, agility, and results.
InterVision delivers leading AI services for every step of the journey, from getting started with AI to developing policies, leveraging hyperautomation via agentic workflows, and setting up POC environments- all aligned to your business goals.
Our team has decades of experience and hundreds of certifications with AWS, Microsoft, Cisco, Fortinet, Juniper, Arctic Wolf, HPE, and many more. No matter your challenge, InterVision can tailor innovative services using best-in-class technology solutions.
Remove obstacles to innovation and leverage InterVision expertise to take advantage of flexible financing choices, exclusive purchasing plans, and simplified marketplace transaction options.
Managed Innovation is InterVision’s unique approach to managed and professional services that drives IT excellence not just today, but into tomorrow. Our success is your success, and our expert team works diligently to continually evolve IT solutions that keep your company ahead of change.
Seamlessly navigate unforeseen IT change with pre-validated solutions from the InterVision NextMove program. Leave unwieldy vendor lock-in and unfavorable contracts behind, while pivoting to next-generations solutions that deliver better performance, costs, and outcomes.
InterVision is a trusted partner for state and local governments, K-12 schools, and higher education institutions. Our expert team can deliver pre-validated solutions and services that deliver better outcomes for constituents and meet complex regulatory challenges.










