By now we’ve all heard various news reports describing the horrific aftermath of ransomware attacks. With an onslaught of new ransomware tactics and increased organization amongst cyber criminals, we’re all more at risk than we have ever been before. You may not sleep well. So, what’s the good news? Rest assured, you can fight back. In this blog, we will answer common questions surrounding ransomware attacks, and explain how you can effectively prepare and protect yourself, your customers, and your organization from this developing threat.
Why Ransomware Is a Problem
According to a recent Gartner® ransomware statistics emerging risks report, the threat of new ransomware models was the top concern for executives in 2021. These new ransomware models are not only more technologically advanced, but they are also highly specialized and organized businesses – making them a worthy adversary for even the largest “most secure” organizations. The same Gartner report states that ransomware hackers are continuing to develop advanced viruses that are designed to linger and infect backup systems. Additionally, these new ransomware viruses do not rely on phishing alone and are harder to identify. This includes newfound attack methods like file-less malware which uses legitimate built-in tools in a system to execute a cyber attack.
The Lasting Effects of a Ransomware Attack
One of the first things to come to mind regarding ransomware attacks is the potential for devastating financial losses. Cyber Security Magazine forecasted global ransomware damage costs to reach $6 trillion by 2022, and predicted that a ransomware attack will be attempted against a business every 11 seconds.
However, there is more to worry about than financial implications. A ransomware attack can halt all business operations while putting valuable company and customer data at risk and financial loss. If a business does not have proper data-safety protocols in place and fails to take immediate and thorough action, irreparable damage to its infrastructure and reputation will occur.
Who Is At Risk?
The sad truth is that everyone is at risk for a ransomware attack. Ransomware is widespread across the internet, and is not limited to specific targets. However, this does not mean that cybercriminals are unable to choose their victims. There are a few preferred targets of cybercriminals who are more at risk than the average person. Norton Security recently defined four target groups who are most at risk for a ransomware attack:
- Businesses with smaller security teams
- Organizations that are able to pay high-priced ransoms, fast
- Organizations that possess sensitive information
- Large businesses in Western markets
What Does Ransomware Protection Do?
The main goal of all cybersecurity protection practices is to stop a ransomware attack from encrypting important files and holding them for a ransom. There are a few free ransomware protection measures available on most devices. For example, Microsoft has a built-in control to help protect devices from ransomware. This basic Microsoft feature ensures folders you choose cannot be altered which prevents them from being encrypted by a criminal. Although free measures like this act as a decent first line of protection for individuals, organizations need an all-inclusive protection plan. This includes purchasing ransomware protection software , ransomware removal tools, and coordinating with third-party cybersecurity organizations. We’ll discuss the best method for protecting your business from ransomware attacks in more detail below.
How Can Companies Prevent Ransomware Attacks?
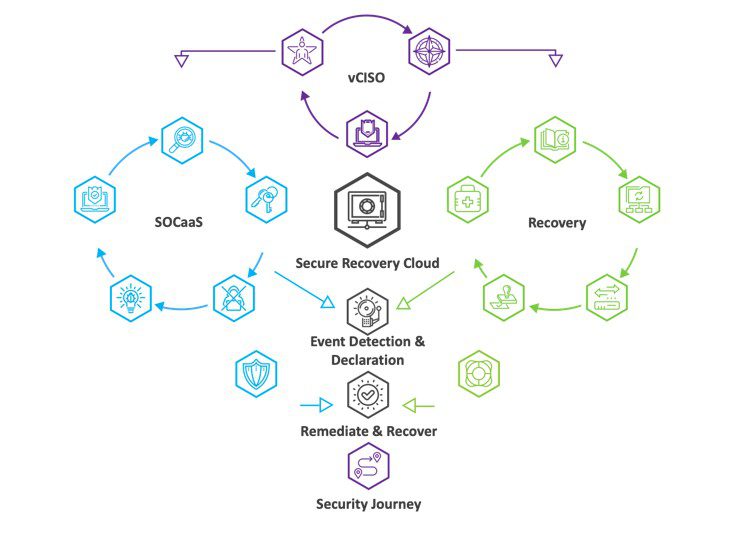
In all likelihood, your business will come under threat from a ransomware attack. And when that happens, you need to be fully prepared. When creating a fully comprehensive cybersecurity strategy, Ransomware Protection as a Service™ (RPaaS™) is your best defense against ransomware attacks. A RPaaS strategy allows you to work with a single provider to develop a cybersecurity solution that encompasses people, processes and technologies, designed to address all protection, detection, and recovery aspects needed to address the evolving threat of ransomware. Here’s a visual representation of Intervision’s RPaaS defense strategy:
At InterVision, our RPaaS solution includes critical operations such as:
Security Operations Center as a Services (SOCaaS): Our security team intercepts suspicious activity and prevents ransomware attacks before they happen. Using methods like multi-factor authentication (MFA) and regular immutable backup processes that prevent any outsider from altering your files, we ensure you’re covered 24/7. SOCaaS provides protection, monitoring, and visibility across the entirety of the client’s threat landscape, both to prevent threats from entering the network and to quickly identify and isolate threats that make it through the door.
- Endpoint Protection: RPaaS ensures that the client has a state-of-the-art EDR solution in place to protect client data on server and workstation devices.
- Broad Visibility: Data from the EDR service and network traffic as well as client security, infrastructure, and authentication platforms, are monitored and analyzed for anomalous behavior 24/7
- Data Enrichment: Information from all sources is correlated together to provide a cross-platform view of potential threats in motion
- Threat Intelligence: Security data is fed into the system from public feeds and developed in-house for more effective identification of threats, both previously known and brand new
- Managed Containment: Compromised endpoints can be remotely isolated by the SOC with client authorization or as part of pre-defined playbooks
Virtual Chief Information Security Officer (vCISO): Ransomware adapts fast, so do we. Our virtual (vCISO) Chief Information Security Officer service, is designed to help your team devise a cyber security roadmap to mitigate business technology risks. vCISO provides a dedicated Senior Information Security team member to guide the maturation of security and risk mitigation. The vCISO will also act as the Incident Response coordinator to an organization during any ransomware threat detections.
- Security Program Maturity: The vCISO will assess the current state of the organization and help prepare roadmaps for improvement using industry standard frameworks.
- Risk Assessment and Management: The vCISO will utilize risk assessment processes to score business technology risk in the environment and develop risk mitigation plans to help improve the risk posture of the organization.
- Cybersecurity Incident Management: Should an event escalate; the vCISO will coordinate incident activities to assure an appropriate and rapid recovery to operations. This may include working with various teams (as needed), including executive/management, insurance, legal, law enforcement, marketing, information technology, cybersecurity, and/or forensics.
Ransomware Recovery: Disaster recovery is an important component of the ransomware protection process. In the aftermath of an attack, our team works tirelessly to identify and contain malicious activity to prevent further damage and recover what has been lost. InterVision’s Managed Restorative Recovery Operations combine best of breed tools, decades of experience, and industry recognized best practices to ensure rapid recovery from any service disruption.
- Recovery Testing: Is designed to emulate a cyber breach and other disasters to ensure goals can be met, and that the DR environment and operations are all performing as expected.
- Recovery Health Management: Data from DRaaS and BaaS components as well as lessons learned from recovery testing all feed an ongoing process of care and improvement for the recovery technologies and DR landing zone.
- Playbook Development: With every recurring test, and outcome the Recovery Playbook is built and updated to ensure the ability to respond quickly in the case of a disaster.
- Replication Operations: InterVision recovery engineers will monitor and remediate issues with replication services and the recovery site.
- Backup Operations: Includes everything from the care and feeding of the backup technologies, to the creation of new jobs or recovery of data.
According to Forbes, an independent global survey of 1,100 IT and cyber security professionals revealed that 80% of the organizations surveyed were hit with ransomware attacks in 2021. In the end, more than 60% of those organizations ended up paying the ransom. This doesn’t have to be you. At InterVision, we’re dedicated to providing you with the best defense possible against this formidable threat. You can learn more about how our RPaaS solutions will give you peace of mind on our website.