This blog post is the third in a series of posts focusing on InterVision’s Managed Cloud Services (MCS). This post describes the technology and tools we use at InterVision as part of MCS. InterVision is an MSP that focuses on cloud and security. Security is woven into everything we do, and we will quickly move to assess and make any critical security changes. In addition to Security, another fundamental principle InterVision has is an “automation everywhere” mindset. The more we automate, the faster things go, and the fewer errors occur. However, we follow engineering best practices and develop automation in development environments because automation can go awry and quickly wreak havoc if done poorly.
When you buy MCS, what happens next?
For each MCS service, InterVision provides the following:
- 24/7 support team
- Customer portal and ticket system
- Set up and configuration of monitoring, logging, and alerts
- Response time SLAs and resolution time objectives as specified in the managed service work order
- Customized escalation procedures for service events
- Support and management of your AWS environment
- Incident response for support services
- Service reporting, including key service performance indicators that include operational metrics, SLA adherence, financial metrics around AWS spend
InterVision has a wide array of managed services and professional services. MCS can be combined with additional InterVision services, including Migration, Cost Optimization, Network, Security, and Service Management services. If desired, we can have our PTaaS team perform penetration testing to identify security issues that InterVision’s teams can remediate during MCS startup.
Once you sign up for MCS, several things will happen during InterVision’s onboarding process. This is where our teams evaluate your environment to identify any anomalies. Depending on what we find during these discovery efforts, some remediation may occur as part of the onboarding. This is essentially a health check for your environment which provides a review against best practices. Still, our aim is not to identify every little issue but to identify anything glaring that should be fixed as part of our taking over the management. Our team will guide you quickly through this stage.
InterVision will provide a project manager to assist with onboarding the customer to the Managed Cloud Service for AWS. InterVision will collect customer information, escalation data, runbook information, service set-up policy information, and other critical data for the successful setup on managed services. During the workload onboarding process, the following will be performed unless otherwise noted:
- Enabling Access Control and Multi-Factor Authentication to the AWS Console
- Addition of Bastion servers (if not already present)
- Implement account-wide environment controls for access control, security, and infrastructure best practices
- Configure monitoring and log collection
- Security assessment of each AWS account and remediation recommendations.
- Additional service-specific onboarding activities are detailed under the description for each service
InterVision will perform a standard set of tasks to onboard customer environments to Managed Cloud Services. If nonstandard or customer-requested tasks fall outside the scope of the typical onboarding tasks, InterVision may require an additional Statement of Work to facilitate the completion of those tasks.
Mandatory Security Services
The following services must be enabled for successful MCS operations (this example is for AWS, but for Azure, we have an equivalent). If these are not currently enabled, they can be enabled during onboarding.
- Customer Bastion Hosts – Bastion hosts will need to be deployed for access to compute resources. Bastion hosts are special-purpose servers that are hardened and host minimal applications, with all other services removed to reduce the threat. They are typically located outside the firewall or inside a DMZ to provide access to untrusted networks.
- CloudTrail – We enable CloudTrail to log all access to resources in the customer environment. CloudTrail is an AWS service that enables governance, compliance, operational auditing, and risk auditing of the customer’s AWS environment. CloudTrail provides logging and an event history which enables resource change tracking and assists in troubleshooting.
- Logging S3 Bucket – A dedicated S3 bucket is used to retain the CloudTrail logs. Access to this S3 bucket is limited to prevent unauthorized access and to ensure that the CloudTrail logs have not been tampered with.
- Active Directory – For Windows Environments, customers will need to provide Active Directory or an equivalent solution to manage users and groups. This can either be dedicated Active Directory servers or the AWS Directory Service, a Managed Microsoft AD service provided by AWS. This is not required if the environment only consists of Linux servers.
- Anti-Virus Software – For Windows server environments, the customer will need to deploy Anti-virus/Anti-malware software solution. InterVision recommends TrendMicro Cloud, but the specific software vendor can be substituted for any enterprise-grade endpoint protection solution. This is not required if the environment only consists of Linux servers.
Recommended Security Services
In addition to the above security requirements, we also recommend the following security features:
- AWS Config – AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. With Config, you can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines.
- Amazon Guard Duty – Amazon Guard Duty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect your AWS accounts, workloads, and data stored in Amazon S3.
- Onboarding Security Checks – During the Onboarding Phase, InterVision will run a security and configuration scanner to detect potential vulnerabilities in the AWS accounts. We will work with the Customer to remediate these during the onboarding process. Any unresolved high-risk security issues would need sign-off by a member of the customer’s leadership team.
Getting your company up and running on MCS
So, there are a set of one-time tasks that occur or our teams to take over the management of your environment and then a set of tasks that occur 24/7 to keep your environment performing optimally.
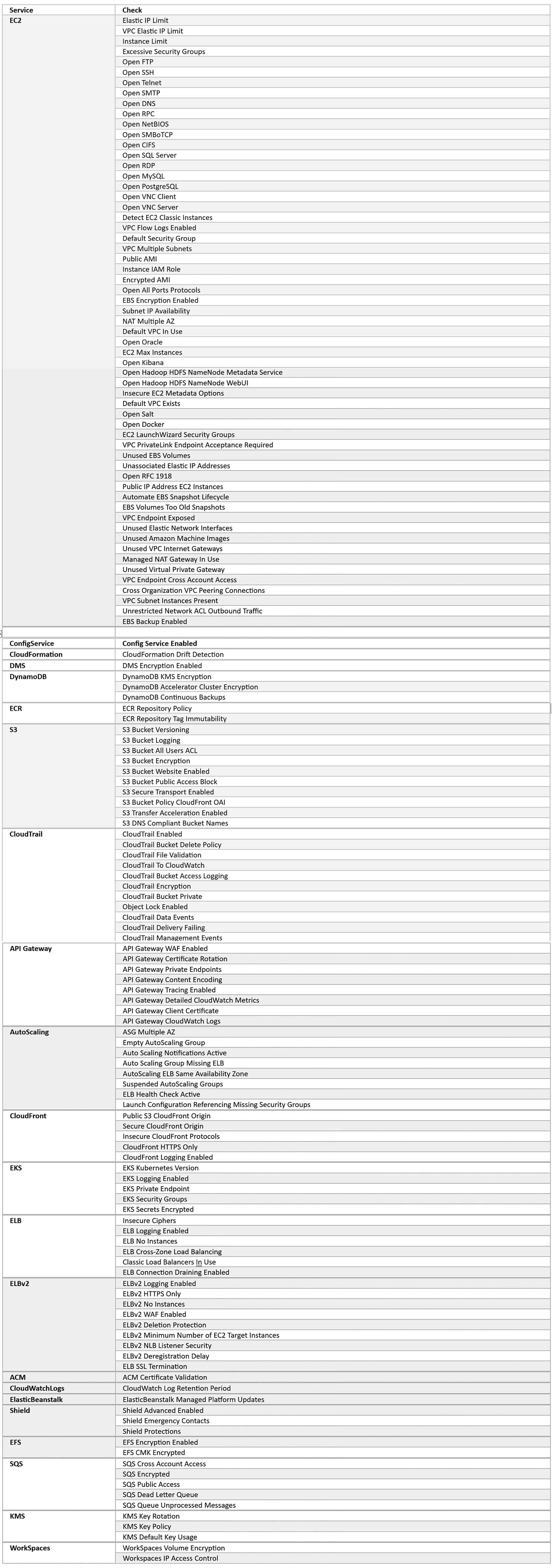
One of the first tools our team will run identifies typical issues (which run into the hundreds). Our team then works with the customer to remediate any issues found. The list below gives you some idea of how extensive these checks are; InterVision continues to modify this list as new AWS services are added and as services change. Again, the focus is to quickly look for any significant issues and get them remediated and then identify long-term items for further analysis.
MCS Foundational Service
For each managed cloud environment, InterVision offers Managed Cloud Foundational Services that compliments and is tailored to the specific managed cloud service you are consuming. This service includes the following:
- Designated team of a Client Service Delivery Manager and Cloud Engineer which complements our 24/7 service desk of Level 2 and Level 3 cloud engineers
- Provides architectural and operational guidance
- Provides escalation management
- Coordinate FinOps and cost management reviews
- Liaison with InterVision technical teams and customer on high-risk changes/projects
- Creation and maintenance of customer runbooks
- SLA reporting
- Facilitates game days sessions that include:
- Accessing EC2 to view Instances
- Launching an Instance
- Connecting to Windows Instance
- Connecting through Bastion Host
- Defining Security Groups and Access settingsConnecting to Linux Instance
- Monitoring walkthrough
- Patching & backup walkthroughs
- Vulnerability & compliance reporting walkthrough (Compliance service required for compliance)
- Facilitate business, service & technical reviews
MCS core offloads the burdens of day-to-day cloud tasks
This MCS core managed service offloads the burdens of day-to-day cloud tasks in seven key operational domains:
- Event and Incident Management
- Change Management
- Configuration Management
- Security Management
- Patch Management
- Continuity Management (Backup & Restore)
- Cost Optimization
I’ll now explain more about each of these operational domains.
Event and Incident Management
- Supported AWS services: VPC, EC2, RDS, EBS, EFS, S3, CloudWatch, Backup Manager & CloudFront.
- VPN Tunnel Support – This service will monitor, alert, and provide response services for the VPN tunnel between Amazon Web Services (AWS)
- Provide 24/7 monitoring and management of the AWS infrastructure via CloudWatch.
- Set up and receive inbound platform alerts and respond to service reliability events, 24/7.
- Troubleshoot and assist with infrastructure issues.
- SLA based response to requests and incidences.
- Operate via Playbooks and Runbooks in providing 24/7 services.
- Respond to support requests from Client round the clock with no limitation on the number of tickets per month.
- Provide ad-hoc support to Client team members and stakeholders.
- Cloud Formation and/or Terraform support
Change Management
- Provide real-time guidance using Service Portal / ticketing system.
Configuration Management
- Configure Service Control Policies to protect from misconfigurations
- Configure AWS Config Rules as requested
Security Management
- Configure Anti-Malware protection
- Configure Access Control Lists and Security Groups (for newly created environments.)
- Audit and remediate Access Control Lists (for existing environments)
- Customer will manage their users via an approved directory service provided by customer.
- Set up AWS GuardDuty as requested – Response to GuardDuty alerts is CUSTOMER responsibility.
Patch Management
- Quarterly patching of all servers and guest OS services
- Coordinate with customer for service-specific patching within scheduled maintenance windows
- Perform patching to address service-impacting bugs (based on patch availability)
Continuity Management (Backup & Restore)
- Configuration of backup policies using AWS Backup service to meet business recovery objectives.
- 24/7 availability to restore data as requested to restore services
- Restore actions from specific snapshots can be performed by customer request
- Point-in-time RDS restore requests
Cost Optimization
- Right-size the infrastructure and reservation management as needed
- Audit S3 bucket usage and implement intelligent tiering or lifecycle management policies as appropriate
- Implement S3 lifecycle policies and recommend storage tiers for S3-based savings
- Recommend reservations and Savings Plans
- Implement cross-account VPC peering as appropriate to limit cross-account network traffic to the private networks (for customers not using Transit Gateway)
- Implement VPC peering between AWS account to minimize traffic leaving the AWS network
- Recommend new, cost saving solutions as appropriate to replace dated and expensive technologies
- Advise business stakeholders with cost control, budgeting and forecasting recommendations
In the next post, I will dig more into the processes and teams of people that drive and support InterVision’s MCS.
